Guides

How to setup an IPv6-only network with NAT64, DNS64 and Shorewall
Goal
The goal of this article is to help people to set up a network that is IPv6 Only (except for the gateway) and does allow the users to access IPv4 servers beyond the gateway.
Overview
If you follow the news surrounding the IPv4 exhaustion, you will now that IPv4 is running out of space rapidly (currently Ripe is allocating the last /8 address space). So, it’s time to start thinking about moving to IPv6.
I have been using a 6-in-4 tunnel from Sixxs for a couple of years now, using this i have set up a dual stack network with my own /48 subnet. This setup is fun and made it possible for me to test IPv6 in real life.
I’ve been using this setup for a while now, and thou it’s an improvement on getting ready for IPv6, it still has an IPv4 network as well. The ultimate goal should be to use only IPv6 in my internal network. The downside of such a network is the fact that i would be unable to reach ‘old’ IPv4 servers which haven’t got an IPv6 address.
To solve this, i decided to configure an IPv6 only network in a test environment, using NAT64 and DNS64. DNS64 basically provides IPv6 addresses for hostnames which only return an IPv4 address, using a prefix. NAT64 accepts connections to those special IPv6 addresses and translates the connection to a IPv4 connection. It’s doing the same thing as normal NAT, translating IP addresses, just across different IP versions.
I’m using this guide as a form of documentation. I might go a bit fast through a couple of sections, but that’s mainly because i assume you are able to configure a basic Bind9 server or Shorewall setup.
It’s also important to note that i will not provide exact commands to install a package, but all of the packages should be available in most package systems (aptitude/apt, yum, …).
Initial setup
Lets start with making an overview of my setup, and what information you should need to set this up.
My gateway is a Ubuntu 12.04 LTS server which is connected to 2 networks and has a Sixxs connection using AICCU, which is configured to start at boot. In total this gives me 3 interfaces (and loopback, but we’ll disregard that).
Interfaces configurations:
- eth0: DHCP (internet)
- eth1: Static IPv6: 2001:1d3:7f2:10::1/64 (you receive a /48 from Sixxs, split it up in at least /64 subnets)
- sixxs: IPv6-in-IPv4 tunnel
List of software used. This contains only daemons specific for this guide:
- Bind9: DNS server
- Shorewall
- Shorewall6
- radvd
I’ll assume that your gateway is able to connect to the internet using DHCP on the eth0 interface, which provides you with an IP(v4) from your ISP and that your Sixxs tunnel is configured.
Bind9
Configure bind9 as you like, just make sure you have configured forwarders that can be used and recursion is enabled.
Shorewall
Make sure IP_FORWARDING=On. Here are my basic configuration files:
Zones
|
1 2 3 |
#ZONE TYPE OPTIONS IN OPTIONS OUT OPTIONS fw firewall net ipv4 |
Interfaces
|
1 2 |
#ZONE INTERFACE BROADCAST OPTIONS net eth0 detect dhcp,tcpflags,routefilter,nosmurfs,logmartians |
No need to add eth1, as it does not have a IPv4 address.
Policy
|
1 2 3 4 5 6 7 |
########################################################################### #SOURCE DEST POLICY LOG LIMIT:BURST # LEVEL net $FW DROP info $FW net ACCEPT # CATCH ALL all all REJECT info |
For security reasons i drop everything coming in from the dangerous internet…
Shorewall6
As with Shorewall, make sure IP_FORWARDING=On. The purpose of this configuration is to block all IPv6 traffic coming in from the internet, but allow clients connected to the gateway through the internal network, to access the internet through the Sixxs tunnel.
Basic configuration files:
Zones
|
1 2 3 4 |
#ZONE DISPLAY COMMENTS fw firewall net ipv6 loc ipv6 |
Interfaces
|
1 2 3 |
#ZONE INTERFACE BROADCAST OPTIONS net sixxs detect tcpflags,nosmurfs,forward=1 loc eth1 detect tcpflags,forward=1 |
Policy
|
1 2 3 4 5 6 7 8 9 10 11 |
########################################################################### #SOURCE DEST POLICY LOG LIMIT:BURST # LEVEL $FW net ACCEPT $FW loc ACCEPT loc net ACCEPT loc $FW ACCEPT net $FW DROP info net loc DROP info # CATCH ALL all all REJECT info |
Again i block everything coming in from the dangerous internet.
radvd
radvd is used to provide stateless configuration for IPv6 interfaces. After you acquired your subnet from Sixxs and have configured your tunnel, you can setup radvd to provide your clients with the information they need to access the IPv6 network.
My configuration:
|
1 2 3 4 5 6 7 8 9 10 |
interface eth0 { AdvSendAdvert on; prefix 2001:1d3:7f2:10::/64 { AdvOnLink on; AdvAutonomous on; AdvRouterAddr on; }; }; |
Configuring DNS64
Configuring DNS64 is not that hard, you just need to tell Bind that it has to return a special AAAA-record if a client from a specific range requests the IP address of a hostname that has no AAAA record. This AAAA-record is constructed by bind, using a prefix. When a client tries to connect to an IP starting with the prefix, it will be forwarded (through routing) to the NAT64 setup.
Prefix
First of, you should decide on a prefix to use. This prefix must be part of your personal /48 subnet (so it doesn’t interfere with other possible real IP addresses). You must at least commit a /96 subnet to this prefix.
As 2001:1d3:7f2::/48 is the subnet provided by Sixxs to me, i decided to use 2001:1d3:7f2:ffff::/96 as my prefix.
radvd configuration
We need to make the clients on the network aware of the IPv6 DNS server on the network, so change your /etc/radvd.conf and add the RDNSS option :
|
1 2 3 4 5 6 7 8 9 10 11 12 13 |
interface eth0 { AdvSendAdvert on; prefix 2001:1d3:7f2:10::/64 { AdvOnLink on; AdvAutonomous on; AdvRouterAddr on; }; RDNSS 2001:1d3:7f2:10::1 { }; }; |
Bind configuration
Now we need to change named.conf.options to contain the following section (inside options, for instance after your forwarders):
|
1 2 3 4 5 |
dns64 2001:1d3:7f2:ffff::/96 { clients { 2001:1d3:7f2:10::/64; }; }; |
The clients option makes sure that only clients on the network connected to eth0 can use the DNS64 service.
Configuring NAT64
To configure NAT64, you have to install an extra daemon: Tayga. Tayga creates a new interface on your server which basically is an internal tunnel through which connections to your prefix network are routed and translated to IPv4 connections. This means both firewalls (Shorewall and Shorewall6) need to be aware of this interface.
Tayga configuration
You will have to make some changes in the Tayga configuration (/etc/tayga.conf), here are the settings i have changed and use:
|
1 2 3 4 |
tun-device nat64 ipv4-addr 192.168.10.1 prefix 2001:1d3:7f2:ffff::/96 dynamic-pool 192.168.10.0/24 |
Tayga needs an IPv4 IP address as it needs to communicate with the IPv4 network, it also needs an IPv6 address, but it determines that itself.
The dynamic-pool option is used to select IP addresses for the IPv6 clients. So each IPv6 client that wants to connect to an IPv4 server gets an IPv4 address linked to it in Tayga (so not on the client, only for internal NAT purposes). If you use a /24 subnet, you can basically have 254 clients connecting to IPv4 servers simultaneously. If you need more, you are allowed to use bigger subnets. Just make sure you use the ranges specified by Ripe for internal use.
Shorewall configuration
I choose to configure shorewall in a similar fashion as with the IPv4 trafic, so all traffic from internet is blocked, all traffic to the internet is allowed. You need to make Shorewall aware of the nat64 interface, as it needs to allow IPv4 traffic to go to and from it, otherwise the translation won’t work.
These are the changes i made to the Shorewall (IPv4) configurations:
Zones
|
1 2 3 4 |
#ZONE TYPE OPTIONS IN OPTIONS OUT OPTIONS fw firewall net ipv4 nat64 ipv4 |
Interfaces
|
1 2 3 |
#ZONE INTERFACE BROADCAST OPTIONS net eth0 detect dhcp,tcpflags,routefilter,nosmurfs,logmartians nat64 nat64 detect dhcp,tcpflags,routefilter,nosmurfs,logmartians,routeback |
No need to add eth1, as it does not have a IPv4 address.
Policy
|
1 2 3 4 5 6 7 8 9 10 11 |
########################################################################### #SOURCE DEST POLICY LOG LIMIT:BURST # LEVEL net $FW DROP info net nat64 DROP info $FW net ACCEPT $FW nat64 ACCEPT nat64 net ACCEPT nat64 $FW ACCEPT # CATCH ALL all all REJECT info |
Shorewall6 configuration
You need to make Shorewall6 aware of the nat64 interface, as IPv6 traffic needs to go to and from it.
These are the changes i made to the Shorewall6 (IPv6) configurations:
Zones
|
1 2 3 4 5 |
#ZONE DISPLAY COMMENTS fw firewall net ipv6 loc ipv6 nat64 ipv6 |
Interfaces
|
1 2 3 4 |
#ZONE INTERFACE BROADCAST OPTIONS net sixxs detect tcpflags,nosmurfs,forward=1 loc eth1 detect tcpflags,forward=1 nat64 nat64 detect tcpflags,forward=1 |
Policy
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 |
########################################################################### #SOURCE DEST POLICY LOG LIMIT:BURST # LEVEL $FW net ACCEPT $FW loc ACCEPT $FW nat64 ACCEPT loc net ACCEPT loc $FW ACCEPT loc nat64 ACCEPT nat64 net ACCEPT nat64 $FW ACCEPT nat64 loc ACCEPT net $FW DROP info net loc DROP info net nat64 DROP info # CATCH ALL all all REJECT info |
That should do it. If you restart the services (bind9, radvd, tayga, shorewall and shorewall6), your gateway is ready to provide a IPv6 only network with connectivity to internet, both IPv6 (through the Sixxs tunnel) and IPv4 (through your ISP’s connection).
Clients
You do need to prepare your clients to work on this network. This setup has been created with Linux clients in mind, but i’ll try and give an overview of what needs to be changed if you want to support Windows (7/8) and Mac OS X.
Linux clients
Linux clients need to install the RDNSSD daemon. This daemon will use the RDNSS information provided by radvd and change the /etc/resolv.conf file to include it. This way you won’t need to configure the resolv.conf yourself.
If you do not want to use the RDNSSD daemon, you will have to change your setup and use DHCPv6, which would mean you have to install the DHCPv6 daemon on the gateway and configure it, and install the DHCPv6 client on the client (which is in most cases part of the standard DHCP client of your distribution).
Mac OS X
From Mac OS X Lion on, Mac OS X is able to accept the RDNSS information from radvd. DHCPv6 is also supported. So there is no need for further configuration.
Windows
Windows Vista, 7 & 8 do not have support for RDNSS, you can provide this by installing rdnssd-win32. They do support DHCPv6, however, so it might be easier to just configure that.
Windows XP is just unable to use IPv6 without installing Dibbler. This tool provides Windows XP with DHCPv6 support.
Final thoughts
I kept my configuration simple on purpose, so if you’d like to add complex rules and policies to Shorewall(6) to protect your network, you can do so as you normally would. The only thing to remember is the flow of traffic for IPv6-Only clients to a IPv4-Only server:
|
1 2 3 4 5 6 7 8 9 10 11 12 |
Client IPv6 -> DNS call target (IPv4-only) hostname -> GW IPv6 GW IPv6 -> DNS result (IPv6 address linked to IPv4 target server) -> Client IPv6 Client IPv6 -> packet -> GW IPv6 GW IPv6 -> routes to NAT64 -> GW NAT64 IPv6 GW NAT64 IPv6 -> NAT64 processing -> GW NAT64 IPv4 GW NAT64 IPv4 -> uses standard NAT -> GW IPv4 (external) GW IPv4 (external) -> packet -> Target IPv4 Target IPv4 -> reply -> GW IPv4 (external) GW IPv4 (external) -> Reverses NAT -> GW NAT64 IPv4 GW NAT64 IPv4 -> reverse NAT64 processing -> GW NAT64 IPv6 GW NAT64 IPv6 -> routes to GW (internal interface) -> GW IPv6 GW IPv6 -> packet -> Client IPv6 |
You need to remember that flow, restricting any traffic between (in this articles case) eth0 and nat64 and eth1 and net64 can break your nat64 setup.

Upgrading Redmine from 0.9.x to 1.3.x
Today i was asked by a client to upgrade his Redmine setup from version 0.9.3 to the latest stable version. As his server is running Ubuntu 10.04 LTS and he installed Redmine using the Ubuntu repositories, this wasn’t the easiest or smoothest task i’ve ever done.
I suspected that upgrading from 0.9.3 directly to 1.3-stable would be a nightmare, so i was planning on upgrading to 1.0-stable, then to 1.1-stable, then 1.2-stable and finally 1.3-stable.
All looked well, and i started taking backups. Of course, the whole Redmine installation was setup using the Ubuntu repositories, so clearly, all of the ruby, rails, rake and rubygems packages were from Ubuntu 10.04. Which would cause a bit of a problem, as i needed newer versions of certain packages. So i ran the following commands (after taking backups of course.) to remove redmine and all it’s dependencies and reinstall whatever is necessary to run rubygems, rake and libapache2-mod-passenger.
|
1 2 |
aptitude remove redmine aptitude install rubygems rake libapache2-mod-passenger |
This made sure i had a basic setup. After that i used svn to get all the versions
|
1 2 3 4 |
svn co http://redmine.rubyforge.org/svn/branches/1.0-stable redmine-1.0 svn co http://redmine.rubyforge.org/svn/branches/1.1-stable redmine-1.1 svn co http://redmine.rubyforge.org/svn/branches/1.2-stable redmine-1.2 svn co http://redmine.rubyforge.org/svn/branches/1.3-stable redmine-1.3 |
This gave me the opportunity to just go into the appropriate directory, follow the guide on Redmine.org on how to upgrade and do that for each major release. On occasion rake would throw me an exception stating i needed a gem installed or a newer version installed, but overall that wasn’t a real problem. Just make sure you run
|
1 |
gem install -v=<correct version> <gemname> |
This all went good until i got to the point of upgrading to 1.3. Apparently version 1.3 needs a later release off rubygems. Whenever i tried running rake to do the db migration, i ended up getting the following error:
|
1 2 |
rake aborted! super: no superclass method `requirement' for <rails::gemdependency:0x7f9e87ea7a18>; |
This is a little problematic as the Ubuntu 10.04 LTS repository does not allow for a newer version to be installed from it. My solution was to just get the package from a newer distribution using a backport available thanks to a Ubuntu PPA from Mackenzie Morgan (Thanks!):
|
1 2 3 |
add-apt-repository ppa:maco.m/ruby aptitude update aptitude install rubygems |
This installs a version which can be used by Redmine 1.3-stable. After that, everything looked great, i could log in, i checked the configuration and it worked!
Or i thought… Whenever i opened the issues list of the project, i would get a Server error (500), the log reflected this:
|
1 2 3 4 5 6 7 8 |
ActionView::TemplateError (undefined method `-' for nil:NilClass) on line #28 of app/views/issues/_list.html.erb: 25: 26: < % previous_group = group %> 27: < % end %> 28: <tr id="issue-<%= issue.id %>" class="hascontextmenu < %= cycle('odd', 'even') %> < %= issue.css_classes %> < %= level > 0 ? "idnt idnt-#{level}" : nil %>"> 29: <td class="checkbox hide-when-print">< %= check_box_tag("ids[]", issue.id, false, :id => nil) %></td> 30: <td class="id">< %= link_to issue.id, :controller => 'issues', :action => 'show', :id => issue %></td> 31: < % query.columns.each do |column| %>< %= content_tag 'td', column_content(column, issue), :class => column.css_classes %>< % end %> |
Googling the error returned me to a bug report from version 1.0, which presented me with a simple solution, i just had to run a simple query on the database:
|
1 |
update issues set parent_id = NULL, root_id = id, lft = 1, rgt = 2; |

Ubuntu 11.10 boot problem
Today i had a network issue on my system, so i tried rebooting my Ubuntu 11.10 server which acts like a router, firewall, DHCP and DNS server for my network. Turns out there was a rather big problem with Ubuntu 11.10 if you upgraded from a previous version.
It seems that in Ubuntu 11.10 the directory containing running processes information and lock files has changed, or well, it has for certain programs. This results in a system where certain daemons/programs expect to find sockets in /var/run, while they are present in /run, or vice versa.
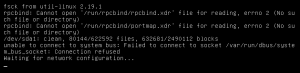
This might result in a boot problem looking like this:
The first lines are not so important, what is important are the last two. It says:
|
1 2 |
unable to connect to system bus: Failed to connect to socket /var/run/dbus/system_bus_socket : connection refused Waiting for network configuration... |
After that last one, you might get that it waits for another 60 seconds for network configuration, but it will get stuck in boot after that.
Luckily i had my 3G enabled phone close, so i could do some searching, which gave me a link to a bug report and a forum post with a fix. In short, few simple steps can help you out here:
- reboot into recovery mode
- start a root shell
- mount the filesystem as read/write:
1mount -o remount,rw / - move everything from /var/run into /run:
1mv /var/run/* /run/ - move /var/lock into /run:
1mv /var/lock /run/ - create symlinks from /var/run to /run and /var/run/lock to /var/lock:
12ln -s /run /var/runln -s /run/lock /var/lock - reboot
Worked like charm here. Hope this helps.